When we want to send someone a message confidentially, even if someone other than us reads the message, if that 3rd party can’t understand what is in the message, then definitely the confidentiality of the message will be secured. So, how can someone protect the confidentiality of their message?
This is where gibberish comes to play. The idea of gibberish is for the third party who comes in between the sender and the receiver. Instead of the real message, what he will see would be some random letters or numbers written. It will be a “gibberish” message to him.
The process of converting a message in standard language to gibberish is known as Cipher.
What is Cipher?
A cipher is an algorithm for performing encryption or decryption; a series of well-defined steps that can be followed as a procedure. There are many methods (different algorithms) that are used as Ciphers. A much famous method is known as Simple Substitution Ciphers, which we referred to as gibberish. This article mainly discusses about the Simple Substitution Ciphers.
Simple Substitution Ciphers
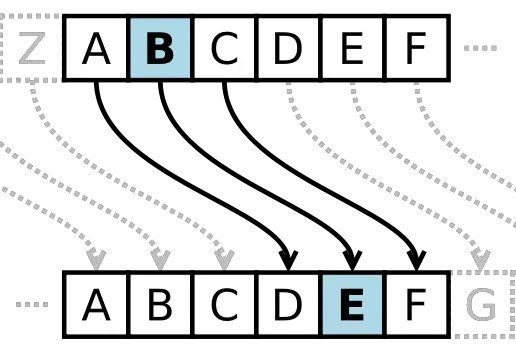
When each letter of an English word (or any other preferred language) is replaced by some other unique letter in a message, it is known as, ‘Simple Substitution Cipher’.
The specific letter assignment is known as the ‘key’ of the Cipher. Usually, it is a table.
The key is a one-to-one mapping (a one-to-one function) from 26 letters in the alphabet to 26 letters in the alphabet.
{A,B,C,D,……..,Z} → {A,B,C,D,……..,Z}
The following table is an example of such a key.
| A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| z | y | x | w | v | u | t | s | r | q | p | o | n | m | l | k | j | i | h | g | f | e | d | c | b | a |
For the sake of understanding, the real language is in block letters and the ciphered language is in simple letters. So if we encrypt the message, “SIMPLE SUBSTITUTION CIPHERS”, the result or the message in gibberish will be “hrnkov hfyhgrgfgrlm xrksvih,” and this is the very reason that these kinds of ciphers are known as ‘Gibberish’.
Caesar Cipher
Caesar Cipher is a well-known historical Simple Substitution Cipher. There is a small story behind it.
As Julius Caesar surveyed the unfolding battle from his hilltop outpost, an exhausted and disheveled courier burst into his presence and handed him a sheet of parchment containing gibberish:
j s j r d k f q q n s l g f h p g w j f p y m w t z l m n r r n s j s y q z h n z x
Within moments, Julius sent an order for a reserve unit of charioteers to speed around the left flank and exploit a momentary gap in the opponent’s formation.
In order to know what was in the message, we should know the key to this Cipher.
The key is not very complicated. It shifts each letter of the ciphered message in the alphabet 5 letters up. So what should we do to ‘v’, ‘w’, ‘x’, ‘y’, and ‘z’, as we don’t have letters to shift them by 5 letters? The answer is in the back of the alphabet. The idea is to consider the alphabet as a cycle of letters where after the letter z, the next letter is a. So the letters ‘v’, ‘w’, ‘x’, ‘y’, and ‘z’ are replaced by ‘a’, ‘b’, ‘c’, ‘d’, and ‘e’ respectively.
If we prepare the key (Cipher table) for Caesar Cipher, it will be as follows;
| A | B | C | D | E | F | G | H | I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| f | g | h | i | j | k | l | m | n | o | p | q | r | s | t | u | v | w | x | y | z | a | b | c | d | e |
So, if we decrypt the message Caesar received;
‘ENEMYFALLINGBACKBREAKTHROUGHIMMINENTLUCIUS,’ which after using proper punctuation and spaces reveals;
‘Enemy falling back. Breakthrough imminent. Lucius.’
Is it easy to break simple substitution ciphers?
If we consider the different methods of Simple Substitution Ciphers, the letter A can be assigned to one of 26 letters, B can be assigned to one from the remaining 25 letters (A is already assigned to some letter), and so on.
So, this will give you altogether 26*25*24*…..*2*1 methods which are 403291461126605635584000000. And that is quite a lot. It seems that breaking these kinds of Ciphers without knowing the key is impossible.
But is it hard as it seems?
The answer is no because the English language is not as random as it seems. Here are some frequently seen facts in the English language:
The letters ‘e’, ‘t’ appears more frequently than the other letters.
The letter ‘q’ is frequently followed by the letter ‘u’.
If 2 letters appear in the same order frequently, there is a high probability that they can be ‘th’. Letters ‘th’ have an average frequency of 168 per 1000 words.
Using of vowels
So, we can use the above facts when we are decrypting a cipher. If we are decrypting a cipher, the first thing to do is to create a frequency table, to see what letters have appeared the most. There is a high probability that those letters can be ‘e’, ‘t’, ‘a’, ‘o’, and ‘n’.
What is left is guesswork and checking using the above-mentioned facts.
Currently, with the development of methods of Cryptography (Cryptosystems), simple substitute ciphers don’t play much of a role. But they are still being used as Brainteasers.
Featured Image courtesy: https://bit.ly/42E3UTo